Table of Contents
This series is designed to help people to understand modern technology, and become more confident in using computing devices. It is not designed to educate experts.
The author is involved in tutoring older students at SeniorNet, a New Zealand wide organisation. SeniorNet hopes that students will feel more confident in using their computing devices as a result of the learning opportunities offered. This series of articles shares that hope.
Your comments, suggestions and questions are welcome in the comment section below.
I wrote this about ten years ago, as part of a course on online scams. I’ve updated it for the changes that have occurred in the intervening years, but most of it remains unchanged and still valid.

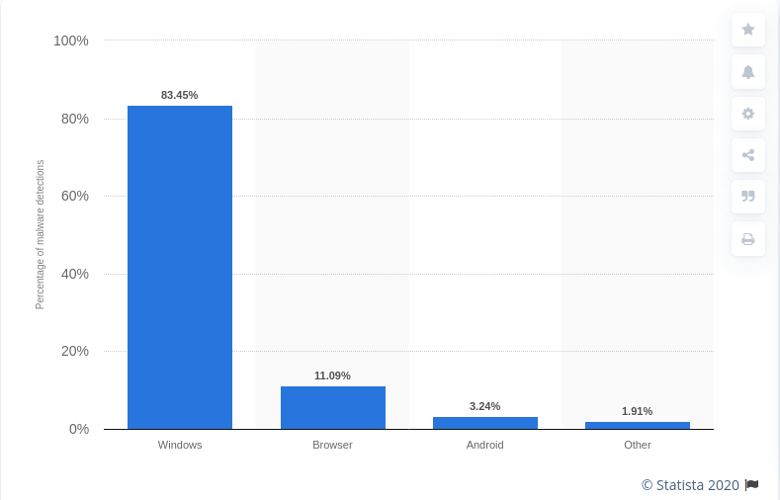
If you see a Microsoft logo when your computer is starting, you are at risk! Most malware is system-specific, and Microsoft Windows is that system.
If your computer has been infected, it may be acting ‘weirdly’. Take action if your computer:
- Wants to connect to sites without you asking (your firewall should tell you).
- Has unusual icons appearing on your desktop or Start menu
- Has extra toolbars on your browser
- Programmes lock up frequently
- Your home page is changed
- Your bandwidth usage increases unexpectedly (a sign you have been recruited into a botnet).
- Your regular system update doesn’t work
- Your malware checker doesn’t update regularly
- Your malware checker and/or firewall stop working (you may not know).
- You can’t access security software supplier sites
- Your contacts tell you to stop sending them spam
In some cases, unobtrusive or covert issues – such as keyboard logging or spyware – may not be obvious. You should:
- review your online transactions regularly (gmail has a link to check the last ten logons, you could pick up a hijacked email account here)
- ensure all activity has been initiated by you
- Contact your service provider immediately if unexplained transactions appear.
- Review your credit card and Bank transactions regularly.
- Review your credit rating regularly. (You can do it once annually for free).
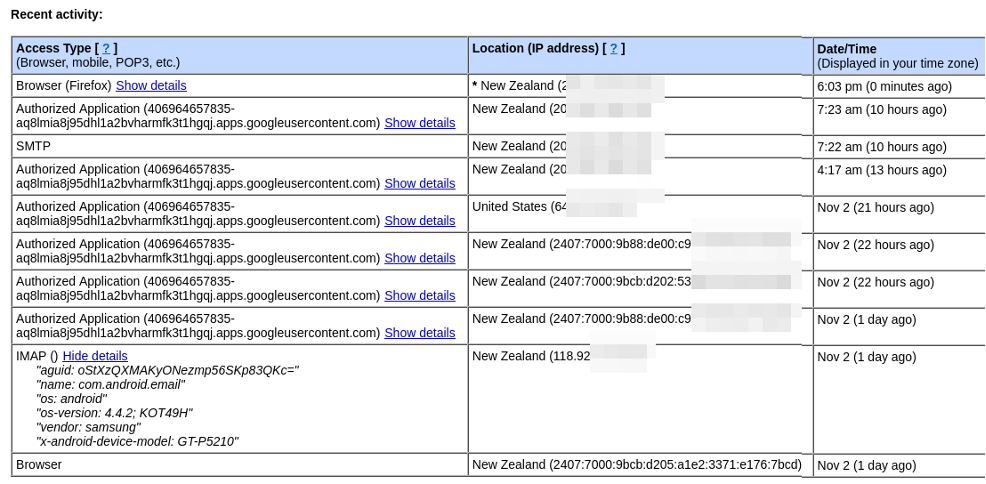
My last 10 gmail log ons.
My last 10 Gmail logons are above. There are a variety of IP addresses, including one USA IP, because some of my logons have occurred using a virtual private network (the subject of another article). One is also via my Samsung tablet, so all are in line with my activities.
The bad news is that much modern malware is designed to give no clues it is resident on your computer.
If you are a nervous person, and are concerned about the 350,000 new Windows malware launched today (or the 350,000 new malware launched tomorrow, or the 350,000 … it will take some days before your virus solution will detect some of these new Microsoft malwares and in the interim, you could be hung out to dry), then forsake Microsoft Windows and move to Linux.
If you must stay with Microsoft Windows (and it’s problems), then use a non Microsoft browser and non Microsoft email programme. This will make you less of a target (but you are still surfing the internet with a bullseye painted on you).
If the loss of a file would hurt, back it up. Backups will protect you from loss in the event of malware infection, software faults, equipment failure or the house burning down (provided they are stored off site). But remember, backup mediums DO NOT have an indefinite life, so back up your backups within the stated lifespan of the backup media. The cloud offers easy backup alternatives.
Read pop ups carefully. Windows style pop ups are a favoured infection vector. Not a problem with Mac and Linux computers which don’t rely on endless pop ups to converse with users.
All operating systems need to be kept up to date to minimise the likelihood of infection. Turn on the automatic update. Windows and Mac computers have been known to slip in unexpected software during updates. Review carefully all details before authorising download if this concerns you.
A modern anti virus solution (now called malware protection) is a MUST for Windows computers. This will give reasonable protection against a range of viruses, trojans, hijackers, fake security software, downloaders and droppers, ransomware, crapware, scareware, keyloggers, rootkits, spyware, diallers, miners and worms. May not protect against unknown threats. There are 350,000 new Windows threats every day.
All computers attached to the internet must have a good quality firewall in place to stop unauthorised inward and outward traffic. Many Windows programmes “phone home”, sending information that you may not authorise. If this concerns you (it should) make sure your firewall denies this activity.
All computers need to have automatic updates in place for all the software resident on the computer. Easy in Mac OSX and Linux, a nightmare for Windows.
Delete spam emails without opening them. They mean you no good. Spam has dramatically reduced recently as the result of the takedown of the Pushdo/Cutwail, Bredolab and Rustock botnets, but spammers will find new avenues. There are plenty of alternative botnets available to the criminals.
Subscribe to an ISP with a good quality spam filter. Check the spam trap periodically as legitimate emails (such as Trademe notifications) have been known to be trapped.
DO NOT CLICK ON LINKS OR ATTACHMENTS IN EMAILS FROM PEOPLE YOU DON’T KNOW. EVER!That is the most important line in this article.
Links and attachments in emails from people you think you know should be treated with caution. Was the email sent to you by a friend, or malware on your friends computer?
Make sure you can see the file extensions (Windows computers only). There are settings to enable this. If your file extensions disappear this might be an indication of malware on your system manipulating this setting.
Use free emails to sign up to services so you don’t end up with unwanted emails from this source. See this article.
Read the Terms and Conditions, and Privacy Policy of services you want to join. It’s a fag, but these statements at least set out what the site might do. Remember that the site might be compromised. Would you be happy for the information to leak? (Who says you need to be fully truthful with the info you provide?)
Be careful of links in web sites. These can lead to unexpected (and dangerous) places.
Searching for a popular subject could deliver you poisoned links leading to sites that wish you harm. Be careful, just because Google delivers, it may not be safe. Google was rated by Trend Micro as the most dangerous site of 2010. Bing and Yahoo search have also been found to be serving poisoned links to searches. Heidi Klum is currently the most dangerous Internet search term! (September 2011).
Be selective in the web sites you use. Warez sites, file swapping sites and adult content sites are all known to host/push malware. Keygen programmes and cracks often carry malware. Pony up the dough to purchase legitimate software, or move to a FOSS platform where programmes are usually free (Linux).
Passwords
- DO NOT REUSE PASSWORDS.
- Use strong passwords
- Store passwords away from your computer (postit notes stuck to the monitor are a definite no-no), or use a password manager.
Avoid downloading stuff from untrustworthy sources. The internet is awash with programmes that will give you Windows specific malware. Not a problem for Linux computers where the available programmes are from controlled repositories. Likewise OS X programmes largely come from Apple controlled sources, but some rogue programmes are loose in the wild.
Stuff that may cause problems includes:
- programmes
- games
- screensavers
- utilities
- Videos (Be particularly careful if you’re told you need a new codec to view a video)
File sharing is a risky proposition. Downloading music or videos from distributed networks means you have no idea where the files are coming from, or what may come with them.
If you must click on a link from a link shortening service (favoured by some crooks to mask the real web site) you can copy/paste the shortened address into the box at https://urlex.org/ to reveal the destination.
Make sure you type (or use ‘Favorites’) to go to web sites where you will be entering login details. Banks and most email providers now provide SSL (https) to make it safer. This may NOT protect you if your computer is compromised by malware which uses man in the middle techniques.
Use an extra layer of security for financial sites. Yes, I know it’s a fag, but so is losing all your hard earned money.
Be wary of email from services you use asking you (on any pretext at all) to provide your login details or personal information. These are invariably phishing emails. Phishing is step one for identity theft. And services you don’t use???????
Use the internet to initiate a credit check on yourself (a great idea because identity thieves can really, really mess up your credit rating). Start here. This is free unless you ask for paid extras.
To help protect against identity theft and any subsequent fraud, you can request that personal identification, that has been lost or stolen, be recorded on your credit file. (same link as above). Typical identification will include credit cards, passport or drivers licence.
When buying on the internet, use plenty of caution. Make sure you are buying from someone reputable. If supplying credit card information this MUST ALWAYS be via SSL (https). No secure connection, don’t supply your credit card details. Shop elsewhere.
Never, ever pay for goods using Western Union. This payment avenue is used extensively in “no goods” scams.
The guiding principal for buying on the web. “If it looks too good to be true, it is too good to be true“.
Be discrete on what personal information you post on the internet. Information you supply could be the first step on identity theft (you really don’t need this). (Facebook and social sites!).
From time to time run a search on your name/details (but not credit card number) to see what personal information is on the internet.
Most importantly, engage brain and make sure your clicking finger works only after instruction from said brain.The second most important line in this article.