Table of Contents
This series is designed to help people to understand modern technology, and become more confident in using computing devices. It is not designed to educate experts.
The author is involved in tutoring older students at SeniorNet, a New Zealand wide organisation. SeniorNet hopes that students will feel more confident in using their computing devices as a result of the learning opportunities offered. This series of articles shares that hope.
There have been many column inches written about the missing emails on Hillary Clinton’s email server. I don’t propose to add to these; the above is just clickbait to get you started on this article. The allegations made against Hillary Clinton are just that, and no more. As far as I’m aware, no court case has ever been prosecuted, and no judgement of guilt made. The presumption of innocence is a legal principle that every person accused of any crime is considered innocent until proven guilty. Therefore, I make absolutely no claims about Mrs Clinton’s guilt, and because of this doctrine assume she is completely and utterly innocent.
Today I’m writing about the software that was at the centre of this furore.
BleachBit.
When the original story hit the airwaves BleachBit was portrayed as some sort of evil software that was used by criminals to cover their tracks, an invention of the devil. But what is it really, and does it have any legitimate uses?

You need to understand how computers work to see how this software fits into the picture.
So let’s delve a little.
Your computer is a very busy little beast, reading and writing files to both RAM (random access memory, also known as volatile memory) and the computer hard drive. When power is cut the information in RAM is lost. The information stored on the hard drive is not lost and when power is restored the data can be read. It’s the files that make their way onto the hard drive that BleachBit is concerned with.
Once a file has been written to the hard drive and then deleted, the file does not get physically removed. Rather, the pointers locating the file get removed. The contents of the file just sit on the hard drive until that space is needed for another file. This can happen within moments, or years later.
I’m a very nosey guy. Some years ago I saw several old computers for sale on TradeMe, and decided to buy them to see what, if anything, I could recover from the hard drives. It turned out the computers had been owned by a grocery business, and I was able to recover a great many confidential documents. It gave me insight into their profit margins, amongst other things. Once I’d enjoyed myself trawling through the secrets I deleted the lot. No doubt the original owners thought they had deleted everything, but they hadn’t. Had I been dishonest, I could have taken and sold the information to the original owners’ competitors.
So what type of files get stored, and what can be recovered?
I use a recovery programme called Photorec. This, like BleachBit, is also an open source programme. I’ve written about my love of open source previously, and you can read what I said here. Because it’s open source it’s freely available. That is, no money need change hands, and there is no onerous license to be complied with. And the major benefit, to me, is the software is effectively audited, so one knows if nasty things have been inserted. What, for instance, is your Microsoft Windows 10 (or 11) telling unknown people about your business or political activities? And what hidden back doors may be lurking, to allow some shadowy three-letter spy outfit access to what you thought was your computer; perhaps as mandated by Sleepy Joe or his minions?
Getting back to the files on a hard disk, what is recoverable? Anything and everything. Pictures, documents, emails, the whole gamut of files and file types. Computers also write lots of control, temporary and log files to the hard drive, and these tend to accumulate over time. This is why computers in general, and Windows computers in particular, tend to slow down over time. This is sometimes called cruft, and while computers have become better at removing this, it still needs specialist tools to achieve a really good, deep clean.
The go-to tool for Microsoft Windows for many years has been a programme called Ccleaner, This programme is now owned by Avast, of virus checker fame, and the free version is now hobbled. There is a Pro version (a paid version) available. Because I use Linux, and there is no Linux version of Ccleaner, I don’t use this software.
There are only three ways to protect your secrets on a computer.
- Don’t put them on a computer.
- Password-protect your secrets (the most commonly used system is called full disk encryption).
- Remove them once you’ve finished with them.
It’s the last of these three scenarios that BleachBit and other system cleaning software aim to solve.
So our questions about the software and whether it has legitimate uses are answered in the affirmative. Any discarded file that you no longer need can, and should, be deleted. Particularly if the computer is leaving your control.
BleachBit or Ccleaner? A good question. There are differences between the two programmes. The user interface of Ccleaner is certainly better than BleachBit’s, but for most users, this is a small consideration.
The two major differences between the two programmes are that BleachBit does not list all programmes and does not perform a registry clean. I see my version of BleachBit now cleans Chrome and Brave browsers so it appears this shortcoming is being overcome. Also, as Linux does not use the registry database system, and any changes to this area can brick your computer, the non-inclusion of this is of no concern to me.
The biggest advantage of BleachBit over Ccleaner, to repeat myself, is that the former is open source. This means it is effectively audited for any inclusions of spyware or government-mandated back doors as was revealed by Edward Snowden. Ccleaner is not open source software, and nobody knows what else proprietary programmes may be doing in the background. As they say, caveat emptor.
The next question you might ask is, can Joe or Joan Public use BleachBit? The answer is “Yes”.
There are a number of good YouTube videos on using this programme on both Microsoft Windows and Linux computers. Just search for BleachBit tutorial in YouTube and you will see how.
The Hillary Killery Setting.
If you want to delete all discarded files by overwriting them (and frustrate the shadowy government agencies at the same time) then one switch is all you need with BleachBit. Use this with extreme care. Once gone, your data is unrecoverable by anyone, God included.
Set your BleachBit System clean as follows:
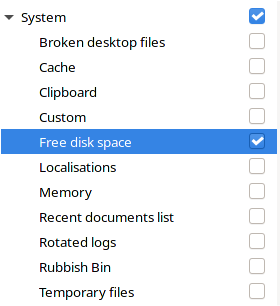
Be aware that the action, once initiated, will take a long time to complete. Mine took an hour.
Downloading BleachBit:
As I’ve stressed, this software is open source. It’s free to download and comes with no onerous licensing terms. Go to the BleachBit website and choose your required edition. Download and install, and away you go.
Unexpected Bonus:
I mentioned using Photorec to recover deleted and lost files. This programme is very handy in recovering files on drives where the file system has become corrupted (I’m looking at you, Windows!). If you have deleted a file, or your file system has become corrupted, then this system could be a lifesaver. Particularly if the files are such that you don’t want someone snooping on your computer (remember Hunter Biden’s laptop?)
If you’ve lost something you must retrieve, immediately turn the computer off so no further files are created. You don’t want to overwrite your just-lost file in your panic.
Download and burn Photorec onto a DVD or USB drive using another computer. Start up the computer with the missing file, using Photorec as the operating system (Photorec uses a cut-down Linux system, and won’t write to your computer’s hard disk unless you tell it to).
Attach a USB drive to the computer to receive the retrieved file/s. I have a couple of large USB drives for this purpose, and the investment is well worthwhile.
Run the file retrieval. I suggest a test run before you need it as you may need to reset your computer’s UEFI settings.
Here are some tutorials for using this software. I see there is a claim on resurrecting encrypted files, but I have grave doubts this would work. The best way to prevent loss of files to ransomware is a good backup regime.
I hope this article has been worthwhile to you.
If you enjoyed this BFD article please share it.